Why Malaysian companies need to transition away from SMS OTPs
By: Joe Seah
Consumers have long been familiar with SMS-based one-time-passwords (OTPs) as a method of authenticating transactions and account activities. Its duration in the market, however, has exposed itself to new vulnerabilities that were previously unconsidered.
Innov8tif Solutions supports Bank Negara Malaysia's initiative to do away with SMS OTPs — urging for more secure authentication methods. Malaysia is not the only one considering the switch, with central banks from Singapore and Philippines pursuing similar initiatives as well. This is mostly due to a new wave of hacking attempts targeting financial accounts that have successfully bypassed the need for SMS OTPs and daily transaction limits.
Local companies are now at a crossroads — either to support this legacy system, or transition towards better authentication methods.
Are OTPs Obsolete?
Not exactly. Let us consider the merits that made OTPs practical in the first place. Unlike passwords, it is:
Only generated upon transaction initialisation.
Only valid for one-time use.
Only valid for a short duration, usually under a few minutes.
Functions as a barrier against fraudsters beyond account access..
With these factors in mind, the vulnerability does not lie within OTPs as a security measure, but SMS as the delivery channel.
Challenges with SMS OTPs
First of all, there are many apps today that can automatically retrieve OTP codes stored within SMS. Several legitimate apps already have this feature baked-in, removing the user's need to switch between apps and memorising the six-digit codes. However, fraudsters can also leverage this exploit, tricking users into downloading third-party apps from dubious sources. Fraudsters can then retrieve OTP codes from the victim's phones whilst remaining undetected.
SMS-based OTPs are also costly to implement, requiring telecommunication infrastructure and services provided by third-party providers. These also represent additional vulnerability points that can be exploited by cybercriminals.
The accountability narrative behind SMS OTPs is also flawed. Fraud victims are often blamed for sharing OTP codes, even though victims are subjected to social engineering tactics, or did not share the OTP codes at all. Service providers play an arguably more important role in the combat against fraud by implementing more secured authentication systems.
Finally, SMS-based OTPs are limited by design — only able to validate the user’s ownership of the registered mobile phone number, which is relatively easy to spoof. This also only represents one out of the three total authentication factors:
What the user owns (mobile phone number, device binding, ID authentication … )
What the user knows (Passwords, security questions …)
What the user is (Thumbprint recognition, facial recognition ….)
Overcoming SMS Limitations
The truth is — SMS-based OTPs are ancient in innovation terms. Hardware and software tokens have taken centre stage in recent years, and have proven to be a reliable authentication method. These methods also rely on OTPs in one form or another.
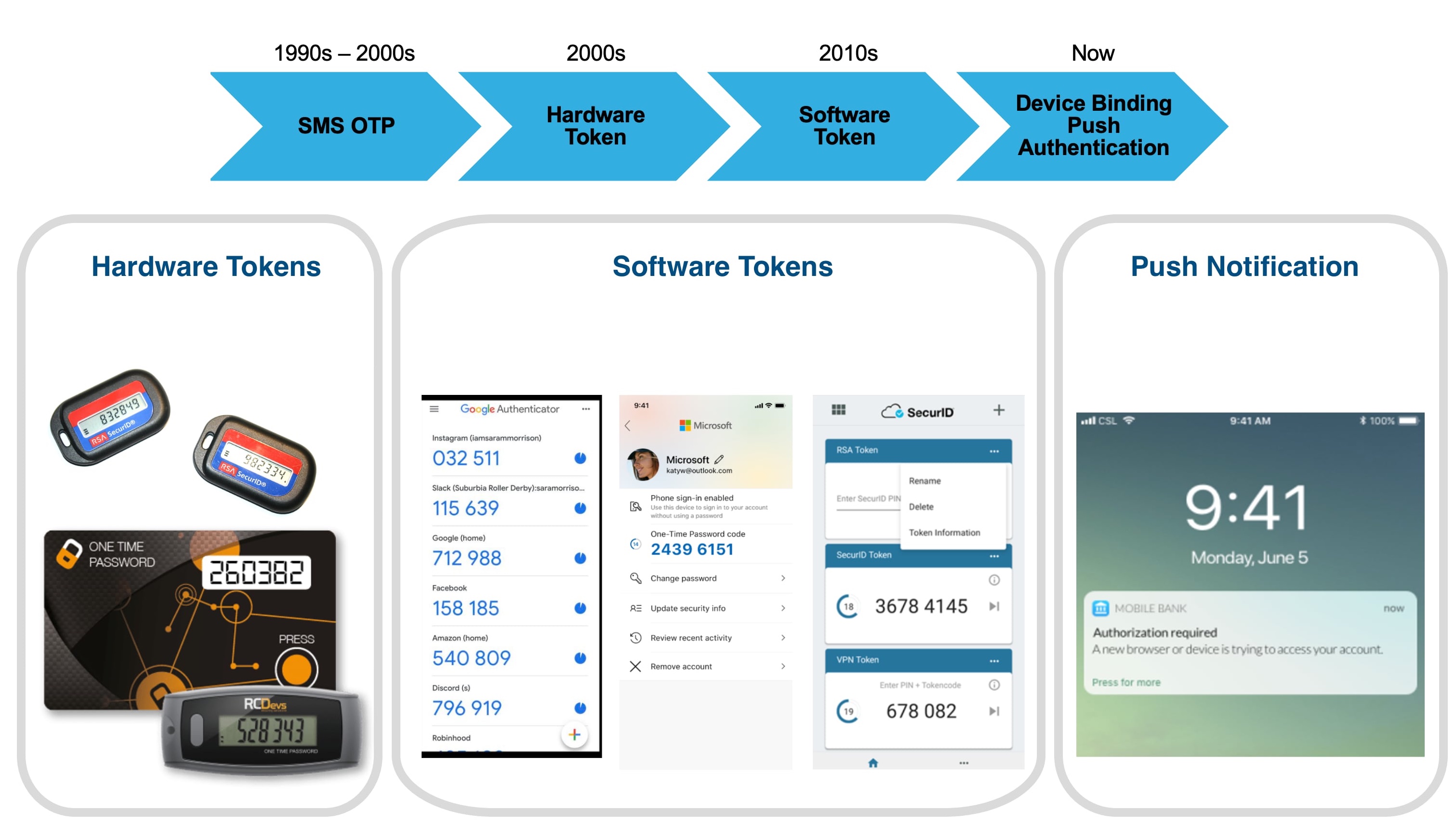
However, these methods also have their own sets of challenges. For instance, hardware tokens are just as expensive to implement and distribute, with the devices prone to being misplaced or lost. Software tokens require users to download an additional app, and are just as vulnerable to social engineering or phishing tactics.
Today, push notifications are the current go-to method — sometimes called passwordless-authentication or frictionless authentication. From the user's perspective, it is just a simple tap on the screen. However, complicated and cryptographic elements are running in the background to ensure that the transaction is properly authenticated. Technical details and compliance standards can be found here: FIDO and EMV3DS.
Customer ID Authentication (CIDA) Ecosystem
To be frank, authentication issues go beyond just SMS OTPs, but the entire authentication system as a whole. What Innov8tif wishes to highlight is the industry's need for a holistic Customer ID Assurance (CIDA) ecosystem. This is due to several key reasons:
Current CIDA systems are heavily focused on silo-ed technology, not processes. For instance, username and password systems are managed separately from electronic-know your customer (eKYC) systems.
SMS OTPs is not the first, nor will it be the last form of secured authentication targeted by regulators. Companies today require solid foundational CIDA systems to make quick adjustments and easily introduce new forms of authentication solutions.
At its core, CIDA is used for fraud prevention, which consists of unauthorised transactions, unwanted account access, fake account creations and so on. Hence, CIDA needs to facilitate quick updates to overcome increasingly sophisticated fraud techniques.
A CIDA ecosystem is needed to take advantage of all user authentication factors: What the user owns, knows, and is.
A solid CIDA ecosystem is needed to maintain a balance of account security, user convenience, user acceptance and scalability.
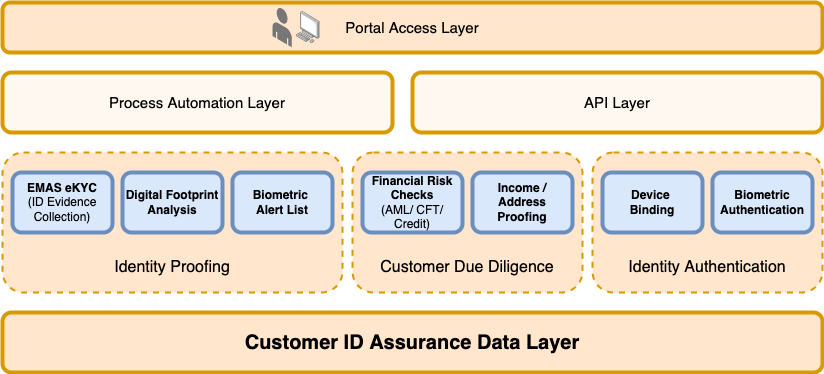
In general, a well-established CIDA ecosystem consists of a solid customer ID database, technologies connected with said database, automated processes and API channels, and a portal that allows companies to interact with the relevant CIDA components.
Within the CIDA framework, solutions like SMS OTPs fall under identity authentication — which is further down the pipeline used to authenticate transactions. However, a robust CIDA ecosystem should start from the beginning at the identity proofing stage. This prevents the creation of fake accounts and mule accounts in the first place.
At Innov8tif, we have helped companies implement CIDA from start to finish. We also specialise in eKYC solutions, using artificial intelligence solutions to conduct facial recognition, liveness detection and ID document authentication for all ASEAN member states. Any other authentication solution is generally built on top of the reliability and results of a robust eKYC system.
For companies looking to protect their user’s account security, our experts are easily reachable at [email protected]. Do visit our website at innov8tif.com to learn more as well.
Joe Seah is the Chief Commercial Officer at Innov8tif Solutions. He hopes to protect ASEAN consumers and companies through the use of secured authentication solutions.
This content is provided by Innov8tif Solutions Sdn Bhd.
Interested in having your announcements on Malaysiakini? Contact the announcements team at [email protected] or whatsapp on +60 17-323 0707 for urgent matters.
RM12.50 / month
- Unlimited access to award-winning journalism
- Comment and share your opinions on all our articles
- Gift interesting stories to your friends
- Tax deductable
